The Acromag APCe7043E is a Non Intelligent PCI Express Carrier Card.
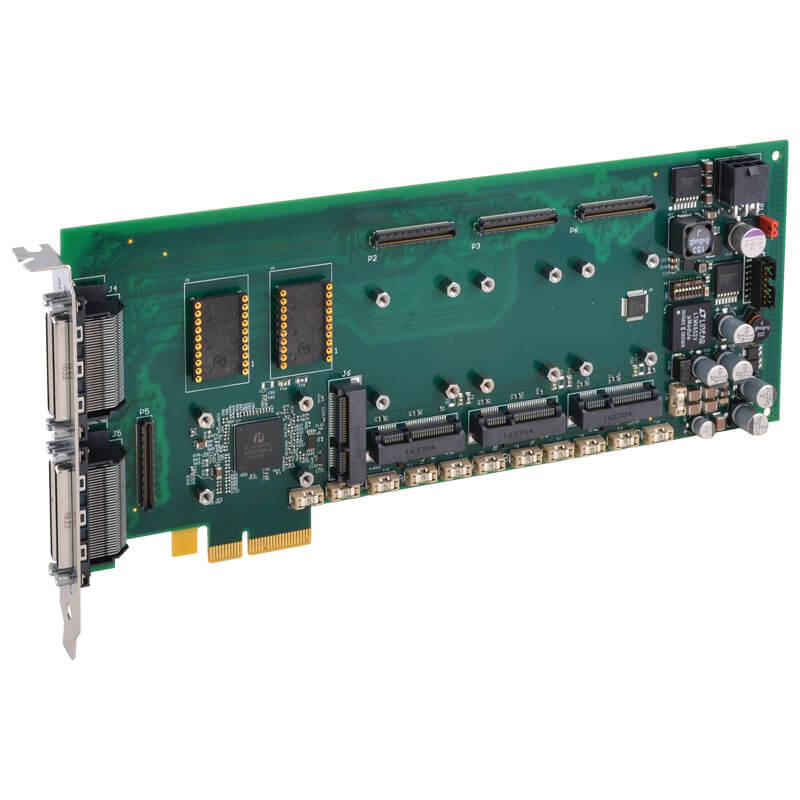
Firstly, the APCe7043E contains four module slots to interface AcroPack or mini PCIe modules to the PCIe bus on a PC-based computer system. The PCIe interface contains 4 lanes that are ¾ length or 25.4cm.
Secondly, by having four AcroPack module slots, you have the freedom to mix a variety of I/O functions. Such as A/D, D/A, Digital In/Out, Serial I/O plus much more on a single board or you can combine modules of the same type to give you more channels. Whatever way you use it; slots are saved as are costs.
AcroPack® product line is based on the Industry Pack I/O Module with a PCIe interface format. They are of a compact size, low cost with the same functionality and memory map of existing Industry Pack Modules. Third Party mPCIe compliant models also useable.
Features of the APCe7043E Non Intelligent PCI Express Carrier Card includes:
- Four AcroPack or mini-PCIe module slots support any combination of I/O functions
- 3/4-length PCIe card (10 inches)
- PCI Express 2.1 compliant, x4 interface
- Plug-and-play carrier configuration and interrupt support
- Fused 1.5V, 3.3V, 5V, 12V, and -12V DC power is provided. A fuse is present on each supply line serving each AcroPack module.
- Front panel 68-pin VHDC1 CHAMP 0.8 connectors for field I/O signals
- Optional isolated power supplies on two slots.
- Support for AcroPacks requiring ±12 V isolated power.
- Extended temperature range DIP switch card identification
- Standard 14-pin Xilinx JTAG programming header
- Software development tools for VxWorks®, Linux®, and Windows® environments.
Finally, for more information, contact us.




Reviews
There are no reviews yet.