This blog on Data in Motion has been provided by our friends at the Crystal Group. To read the original article click here.
Crystal Group are the perfect organisation to discuss “Data in Motion”. That is because the Rugged Servers, Embedded Computers, Network Devices, and other products they manufacture are deal with sensitive information and data daily. Crystal’s products are deployed in Defence, Government and harsh Industrial markets. Therefore, the products are designed, manufactured and tested with the latest configurations for security and safety.
What is Data Motion?
Firstly, Data in Motion can be defined as information moving between systems. Crystal Group discuss a network scenario below. Explaining why protecting Data in Motion is important.
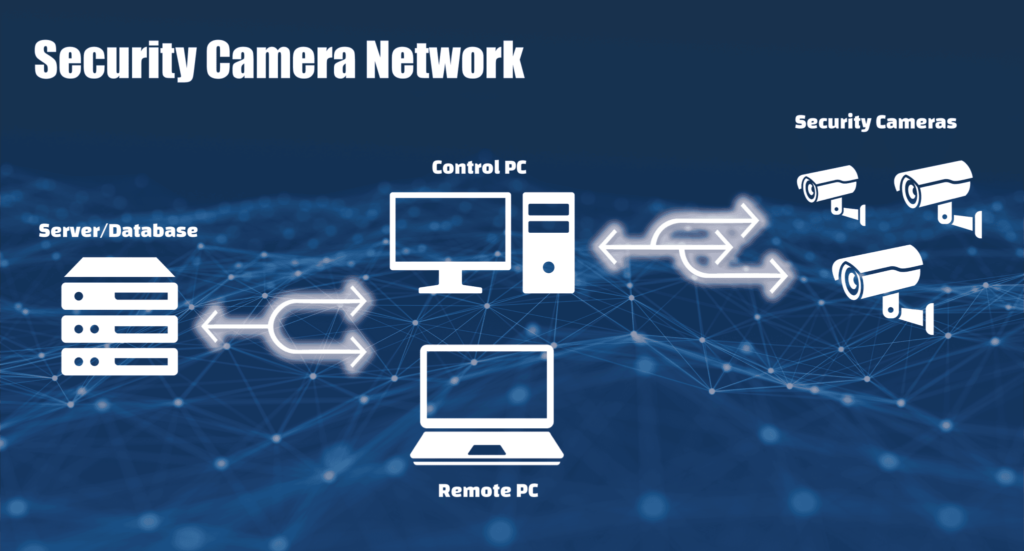
Security Camera Network Example
Problem: A business wants to increase on site security by installing a security camera network to monitor a restricted portion of their property.
The Set Up:
- Each camera is connected to the network using an ethernet cable
- Computer on site allows authorised user to access video feeds and control the cameras
- All camera footage is sent to off site server
- Stores Camera footage in database
- Viewing logged footage is done by remote access using an authorised computer on network
This scenario uses Data in Motion, Data at Rest and Data in Use.
Data in Motion is the topic. It is the easiest to hack. This is because the end systems don’t have control over the data. Plus, they don’t have access to it while it is moving between systems. That is why it is an important consideration for network security.
Data in Motion is vulnerable
- Information is moving between systems
- Could contain credentials for verifying other systems
- Allows remote access to other systems
Potential goals of attackers:
- Steal credentials to impersonate a system
- Gather and store Data in Motion for use in data at rest attacks which take more time
- Control how a system responds to a protocol to get I to a more vulnerable state
- Render a system unstable, known as Denial of Service Attack
How do we protect Data in Motion?
For a recap, Data in motion is the data moving between the server and computers or the cameras and the control computer.
So it depends on the type of attack. Such as:
Sniffing: the most basic attack
- Sniffing allows Data in Motion to be collected or observed for later use.
- Often a precursor to other attacks.
- Attacker sniffs the security camera system credentials moving from the remote computer to the server. They can log in to the server to access video files. Therefore, compromising Data in Use and Data at Rest
- Prevention: Protect by using end to end encryption. Encryption forces the attacker to take additional steps to use the data such as a brute force attack.
Spoofing: Impersonating a system
- Send false or stolen data such as credentials
- An attacker can manipulate a target system
- In Crystal’s example an attacker spoofs a camera by sending bogus footage to control computer
- This breach jeopardises the security of the facility.
- Prevention: taking a zero trust approach to user authentication which requires confirmation of user identity to verify incoming information
Man-in-the middle (MiTM): Controlling the movement of information between multiple systems
- MiTM control allows an attacker to circumvent normal security process or protocols. Such as remote authentication server.
- Crystal’s example: if MiTM attack intercepted a security alert from the control computer and prevented it from being forwarded to the server, users may not be aware of potential breach. Logging of footage could be interrupted while the attack keeps both systems think everything is normal.
- Prevention: User authentication which ensures every end point can be trusted.
Physical attacks
- A physical attack such as cutting network cables or jamming wireless networks.
- The goal of these attacks is usually Denial of Service between systems
- Security camera example: an attacker could physically cut camera lines and no footage would be sent to the control computer. Therefore allowing attackers to enter restricted area unobserved.
- Protection: Tamper detection mechanisms which monitor the status of you protected systems
At the end of the day, there are several ways attackers can infiltrate computer networks and put data at risk. This article discussed the importance of protecting data in motion. Crystal Group hardware and components are built with the security of Data in Motion in mind.
To learn more out Crystal’s great rugged product range, contact us.