This blog on Data in Use has been provided by our friends at the Crystal Group. To read the original article click here.
Crystal Group are the perfect organisation to discuss “Data in Use”. That is because the Rugged Servers, Embedded Computers, Network Devices, and other products they manufacture are used daily, dealing with sensitive information and data. Crystal’s products are deployed in Defence, Government, and harsh Industrial markets. Therefore, the products are designed, manufactured, and tested with the latest configurations for security and safety.
What is Data in Use?
Data in Use is information currently being used in a system. It is generally stored in RAM, swap space, buffers, or registers. Data needs to be used and protected correctly with encryption. Otherwise, the risk of losing the data that you’ve spent time gathering becomes a larger unwanted problem.
To learn more about protecting this temporarily stored data, we return to the network scenario that Crystal Group introduced us to with their Data in Motion and Data at Rest Blogs.
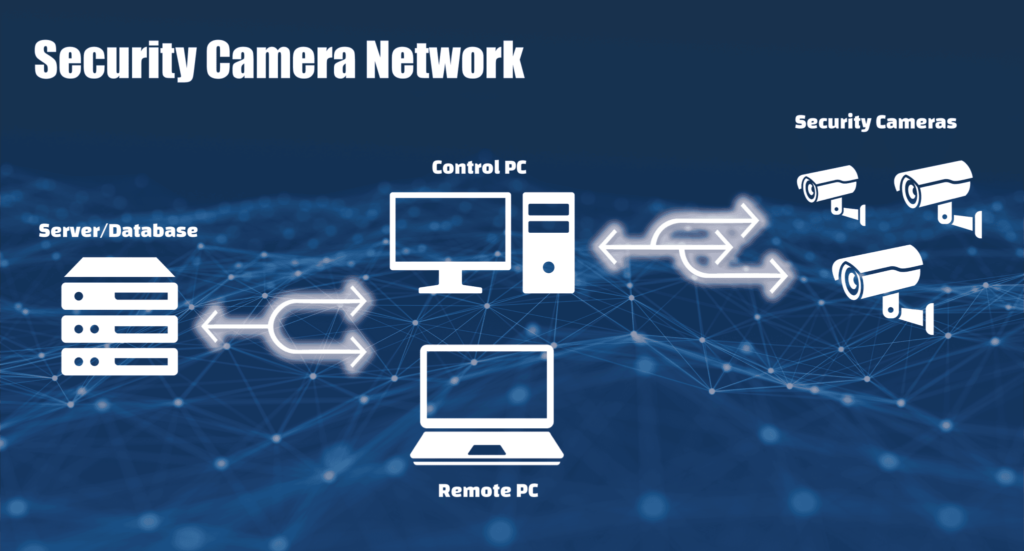
Security Camera Network Example
Problem: A business wants to increase on site security by installing a security camera network to monitor a restricted portion of their property.
The Set Up:
- Each camera is connected to the network using an ethernet cable
- Computer on site allows authorised user to access video feeds and control the cameras
- All camera footage is sent to off site server
- Stores Camera footage in database
- Viewing logged footage is done by remote access using an authorised computer on network
This scenario uses Data in Motion, Data at Rest and Data in Use.
The final area of focus for the Security Camera Network is Data in Use. So temporarily stored data doesn’t have the vulnerability of being accessible outside the system like Data in Motion. In addition, it does not have the vulnerability of being accessible outside the system like Data at Rest. So why does it need to be protected?
Data in Use needs to be protected. Why?
Firstly, Data in Use is important. This is because it is the information your system is currently using. Therefore, those applications running require configuration information and / or information to allow program execution. Otherwise, if an attacker alters this information that a behaviour depends on there can be serious consequences on the running of the program and security of the system.
Why would attackers target Data in Use?
Vulnerabilities:
- Other programs on the system
- Social Engineering
- Successful attacks can be hard to detect
Goals of attackers:
- Altering configuration information
- Obtaining sensitive information such as keys or credentials
- Bypassing authentication
- Holding systems for ransom
How do we protect Data in Use?
From the example, data is use is the data being used in the server database, control PC, remote PC and security cameras. Attackers have access to these systems in one way or another. Whether this be direct physical access. Or installing malicious software by phishing. Therefore, keeping best security practises in mind while using your system can avoid the installation of malware.
Social Engineering: email or text message manipulation
Attackers often use social engineering tactics. Such as sending an e-mail and trying to trick you into giving your password. So, if you do get an e-mail from someone you don’t recognise, examine it carefully before proceeding. Be suspicious of emails that claim you must click, call, or open an attachment. If it looks like a scam, it probably is.
Code injection: digital misdirection
Firstly, code injection attacks are when an attacker changes a program’s execution code to do something different. This alteration my allow the attacker to skip portions of the program. Such as the authentication steps and jump into another program’s memory.
In the example, an attacker that can inject code into a server database could lock up the application that is logging the camera feeds, preventing the information from being stored. Therefore, to protect against code injection, use memory enclaves as a form of user authentication. Thorough testing during software development and hashing algorithms to verify the contents of the memory enclaves should be conducted.
Privilege escalation:
This uses an existing vulnerability in a program to grant elevated privileges to a user or grant access to information reserved for other programs/users. Jailbreaking is another example which allows the running of programs or access information to another program that they normally couldn’t.
In our example, privilege escalation occurs on the control PC which could allows the attacker to have administrative permissions. Therefore, enabling turning off camera feeds and security notifications while bypassing user authentication. Memory encryption is the principle of least privilege. Keeping software up to date is a way of preventing these types of attacks.
Physical attacks
An example of a physical attack would be a cold boot attack. This is when the attacker freezes a system’s RAM modules to preserves their contents longer and reboots it using their own operating system. The goal is to dump the memory contents to allow the data to become Data at Rest where it can be analysed for valuable information such as encryption keys.
In our example if the remote PC is attacked it could provide access to the server/database while bypassing user authentication. Therefore, System configuration checks, memory encryption and tamper evidence/response are all options that should be considered.
Proper security measures on your computer systems
Proper Security Measures stop data from being targeted or used maliciously. However, data security is on going effort that constantly requires diligence. That’s why the Crystal Group continually helps customers in rugged applications protect hardware, components and data from security attacks.