This blog on Data at Rest has been provided by our friends at the Crystal Group. To read the original article click here.
Crystal Group are the perfect organisation to discuss “Data at Rest”. That is because the Rugged Servers, Embedded Computers, Network Devices, and other products they manufacture are used daily, dealing with sensitive information and data. Crystal’s products are deployed in Defence, Government and harsh Industrial markets. Therefore, the products are designed, manufactured and tested with the latest configurations for security and safety.
What is Data at Rest?
Firstly, Data at Rest can be defined as when data is currently being stored in a system. Data storage could be data on a hard drive, flash drive, SD card or other devices. Explaining why protecting Data at Rest is important.
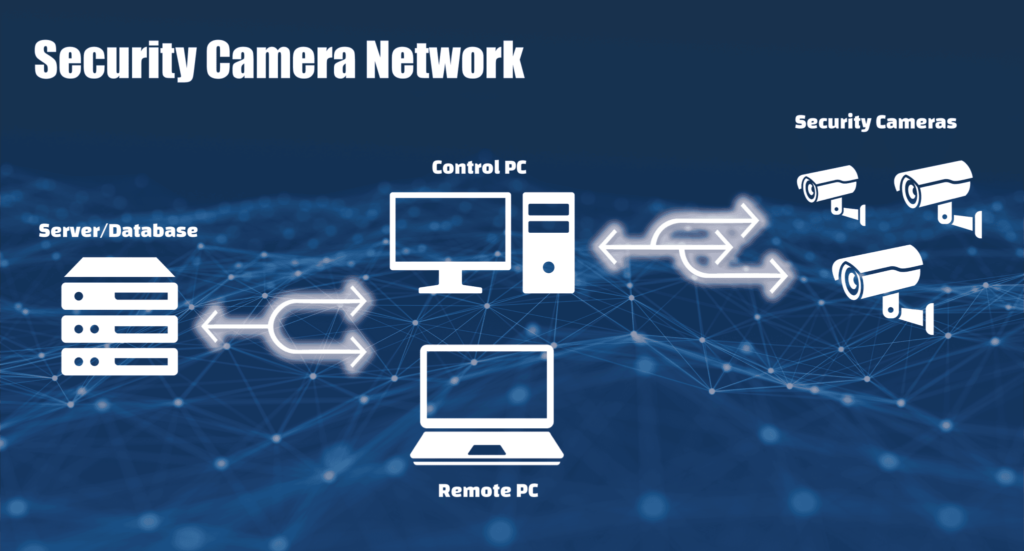
Security Camera Network Example
Problem: A business wants to increase on site security by installing a security camera network to monitor a restricted portion of their property.
The Set Up:
- Each camera is connected to the network using an ethernet cable
- Computer on site allows authorised user to access video feeds and control the cameras
- All camera footage is sent to off site server
- Stores Camera footage in database
- Viewing logged footage is done by remote access using an authorised computer on network
This scenario uses Data in Motion, Data at Rest and Data in Use.
Firstly, Data at Rest is the topic. Whilst, Data in motion is vulnerable because it moves between systems. Data at rest is vulnerable because it always there. All an attacker has to is to obtain a drive storing the data and they will have immediate access to that data. The owner will have no idea that it has been compromised.
Data at Rest is vulnerable.
- Data at rest is persistent and copies can be made
- May contain valuable and useful information about a person, company or system
- Storage Media can be physically removed from a system
Potential goals of attackers:
- Run algorithms to get encryption keys or credentials
- Collect data to assemble a bigger picture
- Deny or prevent access to stored data
- Collect data for malicious use
How do we protect Data at Rest?
Referring back to the security camera example. Data at Rest are the video files being stored in the database. The configuration information is stored on the network systems. Several ways hackers can attempt to compromise the data. Such as:
Scraping: collecting data for later use
- Scraping collects Data at Rest for later use.
- Also collects many small pieces to form a bigger picture.
- Attacker scraping database could determine the security camera coverage patterns over time. This allows them to find blind spots in the system. Find other pathways to enter undetected.
- Prevention: User authentication and encryption of data.
Brute Force Attack
- Even if data at rest is encrypted or locked behind user authentication – it is still vulnerable.
- Brute Force Attack is where the attacker cracks credentials or keys allowing access to otherwise secure data.
- In the security system example – the attacker obtains unauthorised access through brute force login attempts. Try to copy data and use it to obtain system encryption keys and therefore bypassing protections
- Prevention: regularly change encryption keys and credentials.
Physical attacks
- A physical attack such as removing or destroying drive of Data at Rest
- Also the attacker may want to prevent access to data. At worst, attacker might be able to insert the drive into another system to gain access.
- Security camera example: What if an attacker could want to obtain drives from server? Therefore, preventing the company from seeing something incriminating on recorded video feed or perform a brute force attack compromising network security.
- Protection: Site Security, tamper evidence and response and user authentication may protect Data at Rest
Finally, at the end of the day, there are several ways attackers can infiltrate computer networks and put data at risk. This article discussed the importance of protecting data at rest. To review article about Data in Motion, click here. However, in Crystal’s next article they discuss Data in Use and how to best protect your systems using Crystal Group Hardware and Systems.
Therefore, for more information on the Crystal Group product range in Australia, contact us.